How can we prevent Computer Viruses

Anti-Virus Software: Can We Trust It Anymore?
One of the downsides of ICT being available to everyone, is that people who wish to disrupt, or otherwise interfere with data and devices, have opportunities to do so. While I was living in the UK in the early 1990’s, I had the opportunity to attend a conference on virus writing. I chose not to, as I am sure there would have been attendance from both those wishing to defend industry, as well as those wishing to learn how to better extort and interfere with legitimate organisations. I’m not sure how this would have looked on my CV.
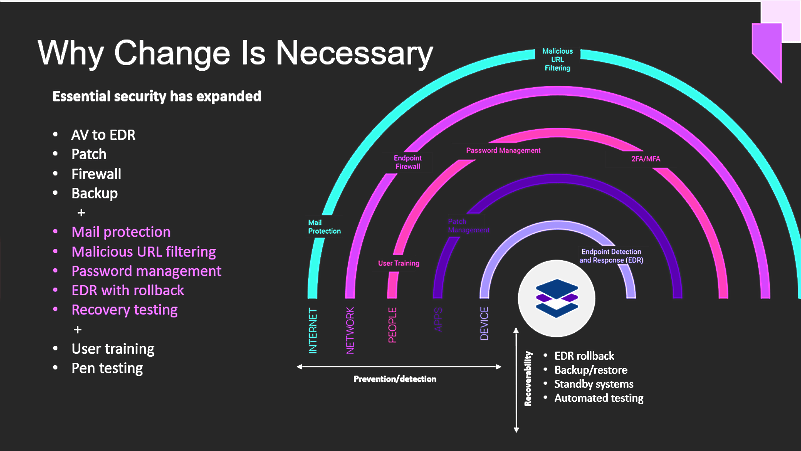
One of the major defences we have against these attacks are the various antivirus tools. IRIS IT highly recommends all customers have at least an industry standard anitvirus. This looks for any previously found malicious code and blocks it from being installed. The tool that IRIS IT recommends runs in the background and looks after its own updates (so our customers do not need to do anything to remain protected). Further it allows IRIS IT to monitor all machines on which it is installed.
There has long been an “arms race” between those wishing to install malicious, unwanted, security defeating and extortion software and those trying to stop it. The consequence of code getting past the antivirus has also increased, with many businesses failing partially or fully because of these attacks. The internet security team at Symantec estimate that nearly a million new threats are released every day. There has also been a 40% increase in directed attacks.
A more holistic approach is now needed to defeat the continuous threats. Endpoint Detection and Response (EDR) are recommended to ensure that your organisation is kept safe. This is designed to deal with threats once they have advanced past your primary protection. So, your protection is made up of two components – first End Point Protection (EPP), which aims to protect your devices by preventing the installation of malicious code, and Endpoint Detection and Response (EDR) which targets threats that have passed your primary protection.
EDR uses continuous file analysis along with artificial intelligence, to detect known threats as well as the actions of malicious agents. This will contain and quarantine the threats, whether they have been previously detected or not.
I was involved in a real-world example of this. While volunteering with a large disability support institute, a staff member followed a link that that lead to the release of a crypto locker. Fortunately, the system was fully and centrally backed up. It took about three hours to complete a “bare metal” restore, taking the system back to the state it was at the last backup (the night before the crypto locker was released). A week later the same staff member followed a similar link and created the same issue. Despite the strongest education, the organisation was cost almost a day of downtime.
With EDR is place, this code would have been detected within the system, and would not have been released.
EPP and EDR need to be considered as insurance. It is something you hope you never need, but if you do, it is invaluable. With this in place, the first you will notice is a report telling you which threats have been isolated – far less stressful than dealing with how to keep your organisation running without your ICT systems.
IRIS IT staff are eager to discuss the best solution for you.
ICT Equipment: To Buy or to Lease?

Having worked with many accountants, and accounts departments, I have seen that there is so much more to keeping an organisation going than the raw profitability. Capital costs (CAPEX), Future costs, Direct Costs, Fixed Costs, Operating Costs, Sunk Costs, Indirect Costs, Variable Costs, Controllable costs, top line, and bottom line seems to keep accountants up at night.
That is before thinking about all the other areas of accounting (Debtors, Creditors. Management Accounting, Supply chains etc.). One of the areas that IRIS IT can help is with the supply of equipment. Our usual approach is to respond to requests for equipment on an ad hoc basis. We only supply quality “tier one” equipment for organisations, and we recognise that compromising on the quality of ICT equipment is a false economy However, ad hoc supply results in organisations having a variety of equipment with various software and operating system versions, along with variable performance. Further this increases Capital Cost (something accountants do not like). IRIS IT will facilitate the lease of your ICT fleet. This means that you can have a standard specification of device, meaning that support is more efficient. Further all devices reach end of life (at a time point agreed – usually three years), meaning that your organisation always has current devices.
IRIS IT have often noted that keeping devices beyond their useful life is unwise. The longer they are run, the more software will be released that will not run on the machine. Also, there is a greater risk of catastrophic failure. While a disk can fail on a new machine, a new machine under warranty will normally be running again within one business day. Older machines can fail such that it can take longer than this to assess whether they are recoverable – and much longer if we are required to recover data due to lack of backup.
Leasing keeps your accountants happy by reducing the capital cost, while reducing your ICT risk by homologising your ICT equipment. Further, build costs can be reduced as a single process can be scripted. Rather than manually setting up each machine, accounting for the differences for each model and software, a single script can be run to create each device identically. This not only significantly reduces the time to get a machine ready – it means that any fault related to the software or operating system will be the same for all systems – and can be corrected en-mass.
So, costs become controlled, machine reliability improves, and support becomes much more efficient.
IRIS IT partners with you to assess the best ICT solutions for you, assessing what is best for your business.